Everything has its birth, maintenance and end of life. This presentation gives an overview of the entire SDLC Process.
Category Archives: Ca
Big Data Analytics – The next best thing
An insight into Big Data and a fresh area of service By Anand Prakash Jangid and Bharath Rao B
History
Civilisation has been built on the foundation of preservation of records and dependence on these records. Hence the importance of identification, Analysis and Storage of records and data was recognized by the dwellers of the past. Ever since, ‘Data’ has been the next most important resource as ‘Time’ being the most important one to mankind. Data has been given high relevance from then on.
Data includes any piece and bit of information which can be recorded and stored to be put in use in the future. Civilization has realised that efficient utilization of data would lead to effective growth. And over the years man has continuously putting efforts to make the best use of data. New ways of capturing data and analytics of the data is being constantly evolving and has now become a field itself. Many terms have been coined for these series of activities. Some of them are Data Warehousing, data analytics and presently is being termed as Big Data.
Big Data Analytics
The industry now has a buzzword, “big data,” for how we’re going to do something with the huge amount of information piling up. “Big data” is replacing “business intelligence,” which subsumed “reporting,” which put a nicer gloss on “spreadsheets,” which beat out the old-fashioned “printouts.”
Big Data is a scientific field of information analysis wherein the following processes are part. They are –
- Data Identification
- Data Source Identification
- Data Storage
- Data Categorization
- Data Analytics
- Data Reporting
- Life of Data
Big Data Analytics is now a huge field of Business itself. Big data is a more complicated world because the scale is much larger. Sophisticated tools have been developed to compliment Big Data Analytics. Open Source tools such as Pentaho, Hadoop, Tabeleau, Splunk etc. are powerful tools used for Big Data. Companies have been incorporated with the purpose of providing Big Data Solutions.
Who uses Big Data?
The Big Data revolution begun immediately after the advent of the WWW also known as the Word Wide Web. Ever since the e-platform was built and stabilized, techniques of using the Internet for Business was developed, and thus, a new market-place was born. Companies who use this market for their business operations use big data to achieve the following objectives –
- Demand and Supply Analysis
- Improvisation of the Product Life cycle
- Better rendering of services
- Market Research
- Customer Behaviour
- Decision Making
- Market Diversification
- Market Penetration
- Product Penetration
There are many classic examples of companies who make of data to achieve the growth that they currently are having. Some examples are as follows –
- Flipkart, e-bay, Amazon (e-commerce giants) use big data to understand the needs of the consumer and hence always publishes those products on their respective websites for sale at a price that the customer cannot refuse.
- Google, Microsoft, Yahoo use big data to understand the browsing patters of the customer and make sure to target the correct advertisements that would be needed to the user. Even their search engines provide those results, against the search phrase inputted by the user, which are of high relevance and would solve the problem faced by the buyer.
- Facebook, Google Plus and other social networking sites use big data for the purpose of Consumer behaviour and give those advertisements, communities, pages etc. that would favour the user.
- Telecom Companies use Big Data to understand the Calling, SMS, Internet and Roaming Patterns of their customers in order to provide better call tariffs and plans so that they capture the entire market.
From the above, one can conclude that, companies use big data so that they are able to capture the customer and more importantly, retain the customer.
Drawbacks of Big Data
Big data in the present era makes use of a lot of data for analytics and storage. This means that the Confidentiality and Privacy of data is now questionable. Privacy concerns are being developing as personally identifiable information is used for analytics. Big Data, no doubt is a powerful tool, but if misused, then the effects can be proven hazardous.
Numerous regulations have been passed by the legislation of various countries to protect the integrity and availability of data and thus the confidentiality and privacy of the data is secured. This entire act of restrictions have given rise to a whole new concept which is called as “Data Localization”.
Data Localization, in simple words, refers to applying of restrictions on the travel and storage of Data to the limit of a geographical boundary.
Analytics from big data may not be always right due to the constantly changing macro and micro factors of environment and change of human behaviour.
Misuse of Big Data Analytics would lead to the following other drawbacks –
- Wrong sale of product and services
- Advertisement Abuse
- Sale of Personally identifiably information.
- Financial Losses
Big Data Analytics as a Fresh area of Consultancy
It is clear that companies harness the power of big data analytics for their growth and Market Presence. It is however not clear to those companies as to “Which is the best way to make use of Data”. There was a proliferation of so-called unstructured data generated by all of the digital interactions, from email to online shopping, text messages to tweets, Facebook updates to YouTube videos. According to computer giant IBM, 2.5 Exabyte’s – that’s 2.5 billion gigabytes (GB) – of data was generated every day in 2012.
Data is only as good as the intelligence we can glean from it, and that entails effective data analytics and a whole lot of computing power to cope with the exponential increase in volume.
Big Data and business analytics are two of the most exciting areas in business and IT these days — but for most enterprises, they are still developmental. Although the opportunities are boundless, the road to an effective Big Data operation is fraught with challenges. Here are some of the obstacles companies are being encountered –
- Budget
- Data clean-up
- Data Retention
- Business and IT Alignment
- Developing new talent
A Chartered Accountant plays a vital role in assisting businesses to improve the use of their resources, increase their efficiency and achieve their objectives. As a management consultant CA can also identify, evaluate and recommend ways to increase revenue and reduce operating costs, analyse operations and suggest changes in structure and individual responsibilities, conduct special studies, prepare recommendations, plans and programs, and provide advice and technical assistance in their implementation. Chartered Accountants by application of their technical knowledge and business experience have been able to cater to the client’s changing needs.
With reference to Big Data Analytics, A CA can render the following Management Consultancy Services –
- Big Data Pre Implementation Preparation
- Big Data Analytics Framework Design
- Big Data Design of Dashboards, Reports and Visuals
- Big Data Assurance
Big Data Pre Implementation Preparation –
A CA based on his knowledge, skills and judgement can firstly help the company to facilitate a smooth big data implementation. While accomplishing this goal seems realistic given the progression of technology and the commoditization of infrastructure, there are common pitfalls that companies, in particular, need to avoid when planning and implementing a big data program. By avoiding these drawbacks, outcomes can enhance an organization’s analytical insights and decision support processes. –
- Developing a business case
- Maximizing data relevance
- Correct Estimation data quality
- Ensuring data granularity is not overlooked
- Contextualizing data in the correct manner
- Grasping Data Complexity
- Facilitating data preparation
- Creating organizational maturity at the correct stage
- Design of data governance methodology
- Consideration of Privacy Laws and Data Localization Laws
- Leveraging on cloud service vendors for implementation of Big Data platform
Big Data Analytics Framework Design –
Preparation for the implementation has to be given the most importance and due care is to be taken for smooth implementation of the Big Data platform. It is the very foundation and depending on the strength that is present in the foundation, further expansion of the platform can be performed smoothly.
The next step is the design of the Analytics Framework. A CA can add maximum value addition as designing the analytics model is the very solution for the Big Data Platform. This model has the following components –
- Data Identification
- Data Categorization
- Linking of Data
- Analytics on the data – It includes performing calculations, ratio analysis, trend analysis, linking of data etc. A CA can leverage the analytical methods that has been given under Standard of Audit 520 which is about Analytical Review Procedures.
- Design of a scoring system and a decision making criteria
- Design of Reports
All of the above constitute the model/framework which would be then tested with data. The data may or may not be live data. However, a CA can facilitate the test.
Upon successful completion of the tests, the framework would have to be implemented in the production/live Big Data Platform. In simple words, the Big Data Analytics tool would be configured to identify the data and capture it from the source, link and categorize the data, perform analytics on the data as per the parameters that have been set, assign scores and ratings on the processed data and generate a report with a conclusion that would facilitate the management to come to a decision regarding a problem.
Big Data Design of Reports and Dashboards –
As Big Data is a implementation of significant size, it would involve many users using the solution. The users would may not be in the same position of the organisation chart. Hence it is crucial that the employee in his respective position of the organisation chart to have adequate access to data which is sufficient, limited and in a logical presentation manner. A CA can facilitate in design of different types of Reports, Dashboards and Visuals that can be used by the appropriate personnel.
Reports –
A Report is a type of visual which would consist of data which is processed, visuals and a conclusion to which a decision can be made by the user of the report. The structure of the report is usually custom made and this design is loaded to the tool.
It is important to note that only those information which is material to the position is displayed in the report.
Dashboards –
A Dashboard is a real-time visual display of various data, reports in the home-screen of the user’s account in the Big Data Platform. A Dashboard would facilitate the user for smooth navigation among the available Big Data inbuilt tools, reports, open items, pending decisions etc. A Dashboard would contain visuals mainly of charts, status updates, links, List of reports to be generated etc.
Big Data Assurance –
This is completely a new field under Big Data Analytics itself. A CA will be able to provide assurance to the client regarding the following scope of activities –
- Privacy Laws and Data Localization Laws are complied with
- Sufficient preventive and detective controls are in place and are continuously monitored against the identified risks
- Ensuring that there is no data leakage from the platform
- Reviewing the Big Data Analytics platform is loaded with the framework that is actually providing the value that is expected by the company.
- Reviewing the storage controls that is implemented keeping in mind of the various Privacy and Data Localization laws
- Reviewing that sufficient and adequate security measures have been deployed to protect the personally identifiable information of others
- Ensuring that the data which is being captured by the Big Data Platform is legal and is from legal sources
Conclusion
Diversification as to, how the decision making strategies are being influenced, is being witnessed. Reliance on Big Data by companies for decision making is gaining momentum. Hence it is very important to influence all to think analytically, think strategically in a total context, deliver insight through analytics, monitor organisational performance in an analytical context, develop innovative business models, use analytics to transform finance. A CA can diversify his services and provide management consultancy services in providing Big Data Solutions to the client. A CA being exposed to variety of business, data, knowledge etc. would be considered the right person to provide solution for a company to implement Big Data Platform. Creativity is the main factor for arriving at a able design of the framework. Hence it is necessary to think out of the Box. Chartered Accountants now have the capacity for rendering a new breed of services which would lead to immense growth and development in the society.
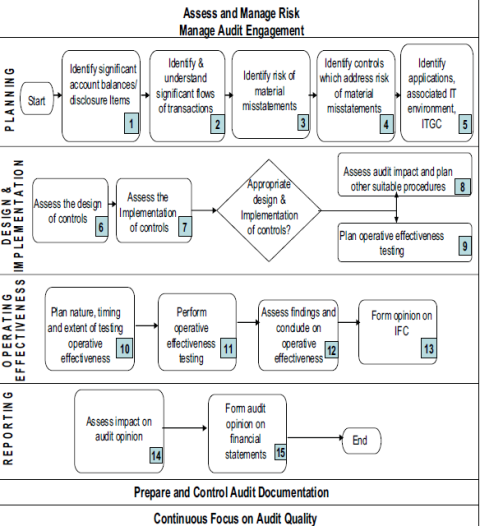
Compliance of Internal Controls over Indian Fianancial Reporting
In the year 2009, we have seen the investor confidence under the Indian scenario falling from Rs. 300 to Rs. 10 per share. The money so invested was systematically wiped off and withdrawn over a number of years by the management of Satyam and falsified its accounts. Satyam had betrayed the trust and belief of its investors. This led to a big blow in the accountability and transparency of Accounts and Internal Controls in India.
Incidentally this problem was highlighted during the Enron, WorldCom and other such scams surfaced the public world-wide.
It is evident that there is a growing need for the protection of the interest of public on companies. The Money invested by the shareholders need to be well protected from ill use and must be used for the sole purpose of the objectives levied down by the company. Apart from investors, various other parties rely on the efficient performance of the companies. They include regulators, bankers, vendors, customers, suppliers etc.
Government as a regulator has an implied responsibility to protect the interest of the public. It has come up with stringent regulations for all those types of business entities that run on public money. To quote a few examples we have the Companies Act 2013, SEBI Act, Clause 49, Multi state co-operative society act etc. Time and again, the Government continues to update the regulation and enforces its compliance by virtue of its regulators. Regulators include SEBI, MCA, and RBI etc.
In the USA, which is known for its benchmark regulations, the Sarbanes-Oxley Act of 2002 was enacted as a reaction to scandals due to Enron and WorldCom and other notable scams The following major sections are enforced on the companies of US origin –
- Section 302 – Disclosure of Controls
Section 302 of the Act mandates a set of internal procedures designed to ensure accurate financial disclosure. The signing officers must certify that they are “responsible for establishing and maintaining internal controls” and “have designed such internal controls to ensure that material information relating to the company and its consolidated subsidiaries is made known to such officers by others within those entities, particularly during the period in which the periodic reports are being prepared.”
- Section 404 – Assessment of Internal Controls
The most contentious aspect of SOX is Section 404, which requires management and the external auditor to report on the adequacy of the company’s internal control on financial reporting (ICFR). This includes documenting and testing important financial manual and automated controls deployed in the company.
Under the Indian scenario, we have the Companies Act revised in the year 2013. This act was revised as a response to the Satyam Scam and to prevent further financial losses. Under the new Companies Act 2013, the following sections pertain to ICFR –
- Section 134 – Directors Statement of Internal Controls being adequate and operating effectively
Clause (e) of Sub-section 5 of Section 134 to the Act requires the directors’ responsibility statement to state that the directors, in the case of a listed company, had laid down internal financial controls to be followed by the company and that such internal financial controls are adequate and were operating effectively.
Clause (e) of Sub-section 5 of Section 134 explains the meaning of the term, “internal financial controls” as “the policies and procedures adopted by the company for ensuring the orderly and efficient conduct of its business, including adherence to company’s policies, the safeguarding of its assets, the prevention and detection of frauds and errors, the accuracy and completeness of the accounting records, and the timely preparation of reliable financial information.”
- Section 143 – Auditor’s assessment on the operating effectiveness of Internal Controls –
The Companies Act, 2013 specifies the auditor’s reporting on internal financial controls only in the context of audit of financial statements. Consistent with the practice prevailing internationally, the term ‘internal financial controls’ stated in Clause (i) of Sub-section 3 of Section 143 would relate to ‘internal financial controls over financial reporting’.
Considering the above, the auditor needs to obtain reasonable assurance to state whether an adequate internal controls system was maintained and whether such internal financial controls system operated effectively in the company in all material respects with respect to financial reporting only.
A company’s internal financial control over financial reporting includes those policies and Procedures that –
- Pertain to the maintenance of records that, in reasonable detail, accurately and fairly reflect the transactions and dispositions of the assets of the company.
- provide reasonable assurance that transactions are recorded as necessary to permit preparation of financial statements in accordance with generally accepted accounting principles, and that receipts and expenditures of the company are being made only in accordance with authorisations of management and directors of the company; and
- Provide reasonable assurance regarding prevention or timely detection of unauthorised acquisition, use, or disposition of the company’s assets that could have a material effect on the financial statements.”
Thus the companies act has created a new challenge for the management to design and implement internal controls over the business processes of the company and even a difficult task to the auditor of testing the design and operating effectiveness of the implemented controls and to check if the deployed controls are sufficient and adequate against the risk that is present in the company’s business environment.
The Management thus have the following responsibilities –
- Identify and Evaluate the risk present in the business environment
- Design a control
- Implement the control
- Monitor the control
- Design compensating controls in-case if a preventive control cannot be implemented.
The management would refer to internal control frameworks such as COSO (Company of Sponsoring Organisations) Internal Control Framework, COBIT 5 (Control Objectives in Information and Related Technology), ISO Standards etc. for guidance of implementing the control.
It is crucial to note that the controls need to be deployed uniformly at all business units of the company. Each control has to be documented and reviewed periodically by the management. The Internal control component can be broken into the following –
- Control Environment – it refers to the company’s entire business environment.
- Risk Assessment – It refers to identification and assessment of the risks present in the environment. This is performed to decide the design of the control.
- Control Activities – A control objective is a statement which emphasis the extent of which the control is to be achieved. A control objective is set after assessing the level of risk that is present in the control environment. These refer to the activities that may be in the form of Policies, Procedures, organisation structure that would be developed and implemented in the company. A set of control activities are mapped to one control objective.
- Information System and Communication – It refers to the IT Controls that have to be implemented in the system. IT Controls can be broadly classified into IT Application controls and IT General Controls.
IT Application Controls vary depending on the applications that have been installed by the enterprise for its revenue generation. Application software is the software that processes business transactions. The Application software could be a retail banking system, an Inventory system or possibly an integrated ERP. Controls which relate to business applications leading to judicial use of the application and enforced through the application itself to the end user are called IT Application Controls.
IT General Controls are those controls other than IT Application Controls, which relate to the environment within which computer-based application systems are developed, maintained and operated and are therefore applicable to all applications These are policies and procedures that relate to many applications and support the effective functioning of application controls by helping to ensure the continued proper operation of information systems.
- Monitoring Activities – These refer to the controls that are deployed by the management which would monitor the regular activities that are performed using the controls. Usually this is performed by conducting periodic reviews initiated by the Compliance team and audited by the internal audit team.
Management would be able to comply with Section 134, if they are successful in designing, implementing and monitoring the internal controls against the identified risks.
The Auditor would have the following responsibilities –
Financial reporting is like singing a success for any organisation. Just as we see a transition from complex classical music to the modern music, there has been a steady change in from Historical Reporting to Responsible Reporting. The need for effective presentation of the results makes a difference in decision making to diverse groups of end users who are spread across geographical bodies. Thus financial reporting makes it a very challenging and a complex exercise.
Because of Section 143, Responsible Reporting now includes that the auditor to provide an opinion on the financial statements and additionally provide an opinion on the operating effectiveness of the internal controls that is in place in the company. Operating Effectiveness refers to the effectiveness of actual performance of the Control in the business environment.
Thus the auditor has now become accountable regarding the financial statements and the internal controls. Penalties would be levied on the auditor by the regulators in case if he has not fulfilled his responsibility of gaining assurance on the effectiveness of the controls.
The Institute of Chartered Accountants of India has come out with a Guidance note for auditors which provides guidance towards their responsibility for Internal Financial controls over financial reporting. This guidance note suggests the following methodology that can be followed by the auditor.
In addition to the above mentioned approach, the auditor will have to ensure that he performs the following tasks –
- Perform Design Effectiveness of every control that is being deployed in every business process, business applications and general applications.
- He would have to obtain sufficient and adequate evidences that would help him substantiate his report in accordance with SA 500. Evidences would include raw system logs, screen shots, tickets, raw files, policy documents, organisation chart etc.
- He would have to test the controls and document the results as part of his work-papers in accordance with SA 230 (Audit Documentation).
- His documentation should include testing lead sheets which would provide the following details –
- Test Date
- Risk, Control Objective and Control Activities and Control Number
- Details of the entity which is being audited.
- Details of evidence provided and the person who provided the evidence
- Completeness check details
- Evaluation of design effectiveness. Design simply refers to a documented blueprint of a control. The documentation includes the control objective and the risks being addressed, the control activities, control owner etc.
- Evaluation of Operating effectiveness.
- Population details and Sampling Methodology.
- Testing Summary of the chosen samples and references to the supporting work-papers created as evidence.
- In case if the auditor would rely on the work of the internal auditor/another auditor in accordance with SA 610/600, he would have to provide his opinion on the quality of testing performed by the Internal Auditor/another auditor.
Thus the ultimate test of Internal Controls is performed here. Based on the inquiries, findings and observations, an Auditor would be able to provide sufficient assurance whether the incorporated controls are adequate and ensuring that there is no harmful effect on the figures presented in the financial statements.
A good chartered accountant loves good challenges and it also means good money, and the big bonus has come out in the form of the companies’ act 2013. It’s only the number which sounds unlucky, but, it is nothing but a baggage of new riverside opportunities. One such opportunity for the Chartered Accountant is his services that he can render to ensure that the company would stay compliant to the Internal Controls over Financial Reporting regulatory requirements and thus he will be able to restore, cultivate and protect the confidence of the investors and other stakeholders of the company.
Cloud Computing – Emerging Opportunities in the CA Profession
Venturing into a whole new level of consultancy and assurance
History and Introduction
We are now part of a system that is revolving around Automation, Flexibility and Convenience. Work at a slow pace is not tolerated. We require the work to be completed at the fastest time and at zero errors. Ever since the advent of computers, man has been able to increase his working speed at an exponential rate. Right from the abacus to the smart phone, newer ways and methods are being developed with the objective of providing Automation, Flexibility and Convenience. The invention of the internet has played a massive role for connecting the world and making it as a global village.
Business have been set up by responsible entrepreneurs and have leveraged these benefits of the computer and the internet. Computers is now part of everybody’s life whether he likes it or not. Computers play an important role in one’s life as it helps in the fields of Education, Medicine, Health, Business, Profession, Industry etc. Thus it is inevitable to progress without the help of the digital magic-box. The presence of internet has grown so large that everything now resides on a network. All the data is present on the internet and is available at a tap of a screen. Yes the phrase “click of a mouse” is now history.
Business on the Cloud
Businesses have capitalised on the cloud to perform their business operations to meet their objectives. The cloud is a concept evolved from the internet which, in simple parlance, refers to, a digital system present on the internet providing a platform to create, store, process and circulate data (SaaS – Software-as-a-Service). This digital system also provides a platform to develop one’s own custom applications (PaaS – Platform-as-a-Service) and provides resources to host those (IaaS – Infrastructure-as-a-Service). This digital system is accessible from any device and from any location of the world. The key benefit of the cloud is that, all of the above mentioned functions is performed on systems that are owned by someone else.
This has resulted in a way of running an enterprise using the cloud. Critical financial transactions run from the cloud. The cloud stores data which are sensitive. Cardholder’s data, Intellectual Property, Business Secrets, Bank Information, Supply Chain Information, Customer and Vendor Data are some examples. Some business functions like swift payments, NEFT and RTGS, Credit Card Payments, Enterprise Resource Planning, Governance, Risk Management and Compliance are performed using the cloud. This is possible as investment on capital expenditure is not required as one would rely on cloud service providers and would incur costs on a subscription based release of payments.
It is crucial that controls have to be in place at critical aspects of the cloud in order to ensure that the confidentiality, integrity and availability of the data is not compromised.
Chartered Accountant and the Cloud
A Chartered Accountant has a unique blend of qualities. A CA can be referred as a Techno-Functional-Legal quality equipped person. Such qualities are developed together only in this profession. A CA can provide enormous value addition in order to develop controls and audit them.
Leveraging on providing consultancy for Cloud Compliance is a path a CA can opt for in providing significant value addition to his client. Operating on the cloud has led to the following risks as per the report provided by Cloud Security Alliance in 2014.
Cloud Threats
At an unprecedented pace, cloud computing has simultaneously transformed business and government, and created new security challenges. The development of the cloud service model delivers business-supporting technology more efficiently than ever before. The shift from server to service-based thinking is transforming the way technology departments think about, design, and deliver computing technology and applications. Yet these advances have created new security vulnerabilities, including security issues whose full impact is still emerging.
The following are identified as critical threats to cloud security (ranked in order of severity):
- Data Breaches
- Data Loss
- Account Hijacking
- Insecure APIs
- Denial of Service
- Malicious Insiders
- Abuse of Cloud Services
- Insufficient Due Diligence
- Shared Technology Issues
Design of a Control Framework
Preparation for the implementation has to be given the great importance. Due care has to be taken for a strong implementation of the Business on the Cloud. Depending on the strength that is present in the foundation, further expansion of the platform can be performed smoothly.
In the design of the Cloud Control Framework, a CA can add maximum value addition as designing the business model is the very solution for the Cloud Platform. This model has the following components –
- Understanding the Business Entity.
- Understanding the Business Operations Standard operating procedure.
- Performing a Business Process re-engineering.
- Design of Automated Internal Control checks in the system.
- Design of Preventive and Detective Internal Controls on the Business Applications and the Cloud Support.
All of the above constitute the model/framework on which the business would now operate on. The controls would be then tested with data. The data may or may not be live data. However, a CA can facilitate the test.
Upon successful completion of the tests, the framework would have to be implemented in the Cloud. In simple words, Cloud would be configured to operate business, cater customers and maintain relationship with the customer and vendors.
A CA can leverage Frameworks like the COBIT 5 Framework and COSO Internal Control Framework. Publications like the COBIT 5 Risk and COBIT 5 Implementation by ISACA and Cloud Control Matrix by Cloud Security Alliance would help the CA to decide on the control objectives and controls that would need to be present in the cloud environment and thus will design an effective control framework.
Audit of a Cloud Control Framework
A CA’s primary role of value addition is Auditing. A CA by virtue of his signature can provide the following Assurance Services to the client with the following scope of activities –
- Privacy Laws are complied with
- Sufficient preventive and detective controls are in place and are continuously monitored against the identified risks
- Ensuring that there is no data leakage from the platform
- Reviewing the storage controls that is implemented keeping
- Reviewing that sufficient and adequate security measures have been deployed to protect the personally identifiable information of others
- Ensuring that the controls enforced by the Cloud Business Applications are operating effectively
- Ensuring that the control design is adequate to the nature and size of the business
The COBIT 5 Framework provides an approach that can be adopted by an assurance professional to provide assurance in an IT Environment. The Cloud Control Matrix by CSA is a Risk and Control Matrix developed in order to have an industrial security benchmark on the Cloud. A CA can leverage these documents to provide assurance as mentioned above.
Regulations
There are many regulations to be complied at different geographical locations. Privacy Laws and Data Governance Laws are the primary two laws that need to be complied at an international level. Bench marked laws like that Sarbanes-Oxley Act, Companies Act 1956, PCI-DSS compliance can be complied by providing adequate consultancy and recommendations to the client on a regular basis. A CA can help the client to comply the ISO 27000 family, ISO 22301, SSAE 16, Companies Act 2013, HIPAA, Sarbanes-Oxley Act etc.
Conclusion
Usage of the Cloud is gaining scope at a tremendous rate on a daily basis. People rely on the cloud as a primary resource to host and control their business. Cloud Computing has certainly paved a new path to Chartered Accountants to provide a fresh line of Consultancy and Assurance Services.
The Digital Detective – E-Investigators as a Service
Digital Forensics as an emerging area of Service.
Digital Forensics has been gaining popularity under the existing consulting line of professionals. Digital forensics is the new field which was introduced and is now provided by Management Consultants recently. This leads to us to believe only one thing, on account of spurt in digitisation of operations the need for digital forensics also has been increasing at an extremely fast pace.
Why is there a sudden demand for Digital Forensics?
The huge demand for digital forensics is being explained as follows –
Preservation of evidence for the court of law – Digital Forensics is primarily performed as an engagement not merely to dig in the hidden or corrupted data however also intended to retrieve and present conclusive evidence to the court of law. The very drawback of information stored in electronic or a magnetic media is that there are very easy to be manipulated and changed. Therefore digital forensics has a bigger objective of preserving the integrity of the data that is written on the media for the court of law at the time of occurrence of the digital crime.
Data Recovery and Analysis – Data Recovery and analysis is the most challenging part in the life cycle of digital forensics. Data is stored in magnetic layered media and it can be easily over written, manipulated and corrupted. Data Recovery is performed in a special lab where the hardware would be treated for recovery of raw data. Data Recovery is also the most longest and the expensive phase of Digital Forensics.
Analysis of the raw data is the next phase of digital forensics. Analysis is usually done by generally running an algorithm which looks for patterns and readily available data on the raw image of the hard-disk. The data would have to be preserved for its integrity. Analysis of data is a challenging task given the condition of the data and the situation which is prevailing at the time of analysis of the data.
Parental Concerns – Internet is very open and dangerous and parents have huge concerns on the information that is being exposed to their children. Terrorism, Pornography, Drugs, Trafficking and Unknown scammers make internet a very dangerous place for children. Children are vulnerable and exposed on the internet. Parents use the help of investigators to find out and track the internet that is being accessed by children and would like to provide protected and guided access to the internet.
Increase in digital crimes on the internet and in corporate environment – Digital Espionage is on the rise on the internet and on the Corporate Environment. Hacking, Data theft, Fake Data, Spyware, Remote Access Trojans and many more are being spread on all networks with the following objectives –
- Data Theft
- Destruction of data
- Manipulation of Data
Information being the most expensive the resource at today’s digital era, one cannot afford any loss of data. Digital forensics would help in figuring out the nature and extent of the data breach that is occurred. Secondly Digital Forensics would help in finding out the extent of which the data that have been manipulated, stolen and destroyed. Finally, digital forensics would be used in finding out “bread crumbs” which would be used to find out the trail used by the attacker while intruding the network.
Intrusion on Privacy of individuals – Applications like Google, Facebook etc. have invaded the lives of every individual. One needs to be very careful with his/her personally identifiable information on the internet in this era of free flowing digital information. If there is any misuse of the data that is being stored, the privacy laws (like HIPAA, SOX etc.) have stringent measures against individuals who have not taken sufficient measures to protect private data. Digital forensics would be used to find out the methods of storage and the security measures that had been incorporated by the data custodians in order to store the private data.
Forensics in highly specialised areas of the IT Infrastructure – Since technology is changing on a daily basis, a Digital Forensic Investigator needs to keep himself updated of developments at all times. New Areas for committing fraud are being discovered. Some of them where an investigator can provide his services are given as below –
- Computer forensics
- Memory Forensics
- Mobile Device Forensics – BB, Android, IOS
- Network Forensics
- Data Analysis
- Database Forensics
Digital Forensics is a growing toddler in the Management Consultancy Industry. Technological advancements, Regulatory Requirements, Data Integrity issues have led to the situation that there is huge opportunities and growth in the area of digital forensics. Hence professionals with an aptitude for information technology and analytical skills can take up the emerging professional opportunities as a Digital Forensic Investigator – which is both professionally satisfying and financially rewarding.
Role of a CA in Implementing an ERP
published in the SICASA Newsletter of the Mangalore Branch of ICAI in the month of December 2013
Business Expansion and Development is a continuous phase for any Enterprise. In this era where there is technological growth, we now observe a “Big Bang” explosion among the enterprises present all over the world. Enterprises are growing in terms of size and presence, service offerings and product offerings which have all resulted in two things, Economic Growth and Difficulties in Management.
Economic Growth is excellent for any economy as we can witness a better standard of life and many more merits and are welcomed by everyone. However Difficulties in Management of the Enterprise is a matter of great concern as there is considerable amount of items which are at stake. The following are a few difficulties which were faced in common by many growing enterprises, Co-ordination between departments, regulatory compliances, Accounting Frauds, Lack of uniform business processes, communication gaps, privacy of data, data redundancy and too much of paperwork and thus had made the job of managing an enterprise extremely challenging.
Thus a solution called ERP was presented to the enterprises. The magic of the ERP was that literally running the whole enterprise using a single interface. All the business processes, accounting functions, communications etc. were integrated. ERP is an abbreviation for Enterprise Resource Planning. ERP is another genre of software. Major players of the ERP market are SAP (SAP AG), Oracle e-business suite (Oracle Corporation), Microsoft Dynamics (Microsoft) etc. The ERP is used to run the day to day show of the enterprise. Every transaction is passed through the ERP be it an internal transaction or a regular business transaction. General Internal Controls are enforced by the ERP solution. And any and every accounting impact that arises as a result of the above functions is automatically recorded in the required accounting standards are performed by the ERP. Central Administration and a smooth functioning enterprise is an end result.
There is a difference between ‘Installation’ and ‘Implementation’ of an ERP. Installation simply means the representative of the service provider installs the ERP solution on the servers and workstations of the Enterprise. Implementation is a different concept altogether. It refers to configuring the installed ERP to merge the business processes of the enterprise, regulatory requirements, Accounting Functions those are applicable and the Internal Controls that are required to the enterprise. An effective implementation of an ERP would lead to very strict internal controls, accuracy in maintaining books of accounts, savings of time and thus would lead the management to focus more of the time on Business rather than internal affairs.
A Chartered Accountant being an auditor and also as an accountant is aware about the business processes and workflows of an enterprise. A Chartered Accountant can provide consultancy services in implementation of an ERP. A CA can be right best person to provide the correct guidance.
The implementation of an ERP can be broadly categorized into three sections viz. Access, Process and Compliance.
Compliance: Laws and regulations of various countries need to be followed by the enterprise having its presence in the respective countries. Each country may have its own Generally Accepted Accounting Standards. In India we have the Accounting Standards, Ind AS, IFRS as the GAAP to the enterprises as applicable. Other regulations include the Clause 49, the Sarbanes Oxley Act, Data Privacy Acts’ of other countries etc. It is extremely important for the enterprise to comply with every regulation. The ultimate goal of any regulation is to maintain uniformity of accounts and to showcase a “True and Fair” view of the Financial Statements. A Chartered Accountant is known for his superiority in Accounting Knowledge. It is most crucial that the accounting transaction to be passed at the correct point of the workflow. Deciding the accounting policy to be implemented for the enterprise can be performed by the CA.
Process: All the workflows and Processes of various functions of the enterprise have to be implemented. Implementing an ERP is a time consuming process and not a simple task enterprise would opt for will also be the best time to perform a Business Process Engineering. All existing processes and workflows can be redesigned in order to make it smaller and simpler but to retain the level of inflows that are generated by the said function. A process is a series of workflows of a specific function. A CA can conduct a risk assessment on the controls that is present in the enterprise and the new processes can be designed with the motive of mitigating the risk that is there. Internal Controls also can be redesigned and enforced through the ERP. A CA can design the structure of the process and workflows that would be most beneficial to the enterprise.
Access: Access should be given to the end users in a need to know basis and at a Minimum Requirement to the employees. It is essential to have adequate Internal Controls to prevent data leakage and abuse. Segregation of Duties (SODs) is a concept that is being practiced by the enterprises. SOD in layman’s language means the maker and the checker should not be the same person. Deciding the roles and responsibilities that is possible to be performed at the enterprise can be provided by the CA. The Correct combination of the responsibilities and roles to ensure that there is no conflict of the SOD can be designed by the CA.
The successful implementation of the ERP is possible only if the correct solution is presented. Hence it is essential for a CA to ensure that each and every function of the Business of the enterprise is taken care of. All resources are effectively used and no deviations from regulations are to be ensured. In brief, A CA used to provide services like Auditing, Book Keeping and Compliances to the enterprise. We can now observe that the services that could be provided by the CA are increased and there is a heavy dependence from the enterprise on Chartered Accountants. We can now be an architect for the enterprise, give a solution for running their business. Thus with the continuous improvement of Technology, services of a CA is required at a whole new level by the enterprise.
The CIA Triad – Assurance on Information Security
– published in the SICASA Newsletter of Mangalore ICAI in the month of August 2013
Information systems are the lifeblood of any large business. As in years past, computer systems do not merely record business transactions, but actually drive the key business processes of the enterprise. In such a scenario, senior management and business managers do have concerns about information systems. The purpose of IS audit is to review and provide feedback, assurances and suggestions. These concerns can be grouped under three broad heads, i.e. Confidentiality, Integrity and Availability of Data.
The CIA triad is a well-known model in information security development. It is applied in various situations to identify problems or weaknesses and to establish security solutions. In this context, confidentiality is a set of rules that limits access to information, integrity is the assurance that the information is trustworthy and accurate, and availability is a guarantee of ready access to the information by authorized people. The model is sometimes known as the CIA triad.
Why are these three elements important? While a business’ assets may be measured in terms of its employees, buildings or cash on hand, the vast majority of its assets are stored in the form of information, whether it is electronic data or written documents. If this information is disclosed to unauthorized individuals, is inaccurate or deceptive, or is not available when required, the business may suffer significant harm such as the loss of customer confidence, contract damages, regulatory fines and restrictions, or a reduction in market share. In the worst case, a failure to control information could lead to significant financial losses or regulatory restrictions on the ability to conduct business.
Confidentiality: It refers to preventing the disclosure of information to unauthorized individuals or systems. Privacy or the ability to control or restrict access so that only authorized individuals can view sensitive information. One of the underlying principles of confidentiality is “need-to-know” or “least privilege”. In effect, access to vital information should be limited only to those individuals who have a specific need to see or use that information. Confidentiality is necessary for maintaining the privacy of the people whose personal information a system holds.
For example, a credit card transaction on the Internet requires the credit card number to be transmitted from the buyer to the merchant and from the merchant to a transaction processing network. The system attempts to enforce confidentiality by encrypting the card number during transmission, by limiting the places where it might appear (in databases, log files, backups, printed receipts, and so on), and by restricting access to the places where it is stored. If an unauthorized party obtains the card number in any way, a breach of confidentiality has occurred.
Integrity: Information is accurate and reliable and has not been subtly changed or tampered with by an unauthorized party. Integrity includes:
- Authenticity: The ability to verify content has not changed in an unauthorized manner.
- Non-repudiation & Accountability: The origin of any action on the system can be verified and associated with a user.
The term Integrity is used frequently when considering Information Security as it is represents one of the primary indicators of security (or lack of it). The integrity of data is not only whether the data is ‘correct’, but whether it can be trusted and relied upon. Integrity involves maintaining the consistency, accuracy, and trustworthiness of data over its entire life cycle. Data must not be changed in transit, and steps must be taken to ensure that data cannot be altered by unauthorized people.
For example, making copies (say by e-mailing a file) of a sensitive document, threatens both confidentiality and the integrity of the information. Why? Because, by making one or more copies, the data is then at risk of change or modification.
Availability: For any information system to serve its purpose, the information must be available when it is needed. This means that the computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly. High availability systems aim to remain available at all times, preventing service disruptions due to power outages, hardware failures, and system upgrades. Ensuring availability also involves preventing denial-of-service attacks. Assurance that the systems responsible for delivering, storing and processing information are accessible when needed, by those who need them.
It is important to note that confidentiality, integrity and availability are not the exclusive concern of information security. Business continuity planning places a significant emphasis on protecting the availability of information as part of the overall objective of business recovery. Common back office procedures, such as maker/checker, quality assurance, change control, etc. along with such regulatory areas as SOX 404(SOX or Sarbanes-Oxley Act is nothing but the USA version of Clause 49) focus on ensuring the integrity of information.
| CIA | Risks | Controls/Remedy | Primary Focus |
| Confidentiality | Loss of privacy. Unauthorized access to information. Identity Theft | Encryption, Authentication, Access controls | Information Security |
| Integrity | Information is no longer reliable or accurate. Fraud | Maker/Checker, Quality Assurance, Audit Logs | Operational Controls |
| Availability | Business disruption, Loss of customer confidence, Loss of revenue | BCP Plans and Tests, Back-up storage, Sufficient capacity | Business Continuity Planning |
Applicability of CIA Triad made easy
The CIA Triad is entirely concerned with information. While this is the core factor of most IT security, it promotes a limited view of security that tends to ignore some additional, important factors. For instance, while Availability might serve to ensure that one does not lose access to resources, one need to provide information when it is needed, thinking about information security in and of itself in no way guarantees that someone else isn’t making unauthorized use of your hardware resources.
It can be concluded that the fulfillment of the CIA principles and the compliance with the goal of information security is not a goal with a clear end but an open goal that continually changes with time and the development of technology, the means of information security and the emergence of new threats and vulnerabilities. Lasting efforts must be exerted to maintain the confidentiality, integrity and availability of information, it is not possible to take some precautions and declare that the CIA triad is fulfilled and that nothing more should be done.
Moreover, it can be deduced that efforts ought to be exerted not only by information security professionals, but by employees and all holders of confidential information to safeguard the CIA principles.
Sources:
- www.csoonline.com
- www.wikipedia.com
- www.isaca.org
- Information Systems Audit – Ron Weber
Business Continuity Planning
– published in the SICASA Newsletter of Mangalore ICAI in the month of August 2013
Business and enterprises of today depend heavily on information and communication technology (ICT) to conduct business. The ICT plays a central role in the operation of the business activities. This dependence on the systems means that all enterprises should have contingency plans for resuming operations of the business activities. For example, the stock market is virtually paperless. Banks and financial institutions have become online, where the customers rarely need to set foot in the branch premises. This dependence on the systems means that all enterprises should have contingency plans for resuming operations from disruption.
This disruption of business operations can be due to unforeseen man-made or natural disaster that mat result into revenue loss, productivity loss and loss of market share among many other impacts. Thus enterprises have to take necessary steps to ensure the continuity of operation in the event of disruptions.
Business continuity is the activity performed by an organization to ensure that critical business functions will be available to customers, suppliers, regulators, and other entities that must have access to those functions. These activities include many daily chores such as project management, system backups, change control, and help desk. Business continuity is not something implemented at the time of a disaster; Business Continuity refers to those activities performed daily to maintain service, consistency, and recoverability.
The objective of a Business Continuity Plan (BCP) is to enable an organization to continue to operate through an extended loss of any of its business premises or functions. The fundamental aim of BCP is to:
· Manage the risks which could lead to disastrous events.
· Reduce the time taken to recover when an incident occurs and,
· Minimize the risks involved in the recovery process.
The foundation of business continuity are the standards, program development, and supporting policies; guidelines, and procedures needed to ensure a firm to continue without stoppage, irrespective of the adverse circumstances or events. All system design, implementation, support, and maintenance must be based on this foundation in order to have any hope of achieving business continuity, disaster recovery, or in some cases, system support. Business continuity is sometimes confused with disaster recovery, but they are separate entities. Disaster recovery is a small subset of business continuity. It is also sometimes confused with Work Area Recovery (due to loss of the physical building which the business is conducted within); which is but a part of business continuity.
Steps in constructing an effective BCP:
1. Document internal key personnel and backups. These are people who fill positions without which a business absolutely cannot function – make this list as large as necessary but as small as possible.
· Consider which job functions are critically necessary, every day. Think about who fills those positions when the primary job-holder is on vacation.
· Create a list of all those individuals with all contact information including business phone, home phone, cell phone, business email, personal email, and any other possible way of contacting them in an emergency situation where normal communications might be unavailable.
2. Identify who can telecommute. Some people in an organization might be perfectly capable of conducting business from a home office. Find out those who can and who cannot work from home.
3. Document external contacts. If an organization has critical vendors or contractors, then build a special contact list that includes a description of the organization and any other absolutely critical information about them including key personnel contact information.
· Include in the list people like attorneys, bankers, IT consultants etc anyone that you might need to call to assist with various operational issues.
· Don’t forget utility companies, municipal and community offices (police, fire, water, hospitals) and the post office.
4. Document critical equipment. Personal computers often contain critical information
· Some businesses cannot function even for a few hours without a fax machine. Does the company rely heavily on the copy machine? Does the company have special printers that it absolutely must have?
· Don’t forget software – that would often be considered critical equipment especially if it is specialized software or if it cannot be replaced.
5. Identify critical documents. Articles of incorporation and other legal papers, utility bills, banking information, critical HR documents, building lease papers, tax returns. You need to have everything available that would be necessary to start your business over again. Critical Documents would include loan payment schedules, email services bill payments etc
6. Identify contingency equipment options. If your company uses trucks, and it is possible the trucks might be damaged in a building fire, where would you rent trucks? Where would you rent computers? Can you use a business service outlet for copies, fax, printing, and other critical functions?
7. Identify your contingency location. This is the place where the company would conduct business while the primary offices are unavailable.
· It could be a hotel – many of them have very well-equipped business facilities you can use. It might be one of the company’s contractors’ offices, or its attorney’s office.
· Telecommuting for everyone is a viable option.
· If you do have an identified temporary location, include a map in your BCP. Wherever it is, make sure you have all the appropriate contact information (including people’s names).
8. Make a “How-to”. It should include step-by-step instructions on what to do, who should do it, and how.
9. List each responsibility and write down the name of the person assigned to it. Also, do the reverse: For each person, list the responsibilities. That way, if you want to know who is supposed to call the insurance company, you can look up “Insurance
10. Put the information together! A BCP is useless if all the information is scattered about in different places. A BCP is a reference document – it should all be kept together in something like a 3-ring binder.
· Make plenty of copies and give one to each of your key personnel.
· Keep several extra copies at an off-site location, at home and/or in a safety-deposit box.
11. Communicate. Make sure everyone in the company knows the BCP. Hold mandatory training classes for each and every employee whether they are on the critical list or not. You do not want your non-critical staff driving through an ice storm to get to a building that has been damaged by fire then wondering what to do next.
12. Test the plan! You’ve put really good ideas down, accumulated all your information, identified contingency locations, listed your personnel, contacts and service companies, but can you pull it off?
· Pick a day and let everyone know what’s going to happen (including your customers, contractors and vendors); then on that morning, act as though your office building has been destroyed. Make the calls – go to the contingency site.
· One thing you will definitely learn in the test is that you haven’t gotten it all just exactly right. Don’t wait until disaster strikes to figure out what you should do differently next time. Run the test.
· If you make any major changes, run it again a few months later. Even after you have a solid plan, you should test it annually.
13. Plan to change the plan. No matter how good your plan is, and no matter how smoothly your test runs, it is likely there will be events outside your plan. The hotel you plan to use for your contingency site is hosting a huge convention. You can’t get into the bank because the disaster happened on a banking holiday. The power is out in your house. The copy machine at the business services company is broken. Your IT consultant is on vacation.
· Every time something changes, update all copies of your BCP.
· Never let it get out of date. An out-of-date plan can be worse than useless: it can make you feel safe when you are definitely not safe.